
Researchers have found a shortcoming in key security protection recently introduced in the browser plugin for Oracle's Java software framework, a flaw that makes it easier for attackers to sneak malware onto end-user computers.
By default, the widely used plugin doesn't check the status of digital certificates used to sign Java apps hosted on websites, Ars Technica has confirmed. As a result, Java presents certificates as trustworthy even when they've been reported as stolen and added to publicly available revocation databases. The failure of Java to check certificate revocation lists came to light on Tuesday when a legitimate site was found hosting a malicious app. Java presented an accompanying certificate as a trusted credential belonging to Texas-based Clearesult Consulting Inc. even though the firm had issuer GoDaddy revoke the certificate in December.
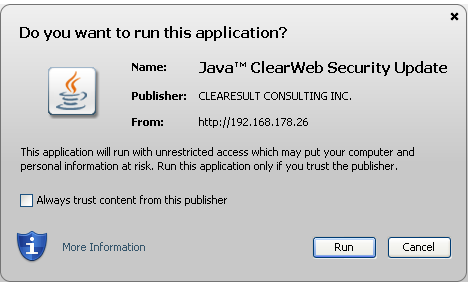
"Java thinks the stolen certificate used is 100% valid and should be trusted," Jindrich Kubec, director of threat intelligence at antivirus provider Avast, wrote in an e-mail. Referring to certificate revocation lists and an alternate method for invalidating credentials known as the online certificate status protocol, he added: "With CRL/OCSP it would make it untrusted and probably present completely different dialogues or even won't allow running the applet at all—unfortunately, the situation is a bit complicated with testing this behaviour, so I can't tell for sure which of the above would be true."
Read 4 remaining paragraphs | Comments