A campaign that forces sites running the Apache Web server to install highly malicious software on visitor's PCs has compromised more than 40,000 Web addresses in the past nine months, 15,000 of them in the month of May alone.
The figures, published Tuesday by researchers from antivirus provider Eset, are the latest indication that an attack on websites running the Internet's most popular Web server continues to build steam. Known as Darkleech, the rogue Apache module gets installed on compromised servers and turns legitimate websites into online mine fields that expose unsuspecting visitors to a host of dangerous exploits. More than 40,000 domains and website IPs have been commandeered since October, 15,000 of which were active at the same time in May, 2013 alone. In just the last week, Eset has detected at least 270 different websites exposing users to attacks.
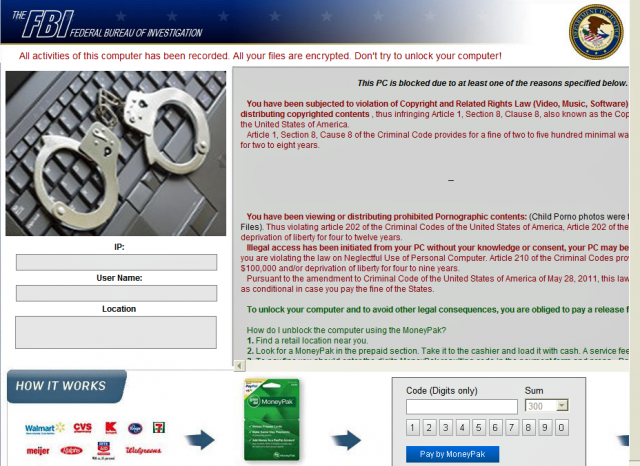
Sites that come under the spell of Darkleech redirect certain visitors to malicious websites that host attack code spawned by the notorious Blackhole exploit kit. The fee-based package available in underground forums makes it easy for novices to exploit vulnerabilities in browsers and browser plug-ins. Web visitors who haven't installed updates patching those flaws get silently infected with a variety of dangerous malware titles. Among the malware that Darkleech pushes is a "Nymaim" piece of ransomware that demands a $300 payment to unlock encrypted files from a victim's machine. Other malware titles that get installed include Pony Loader and Sirefef.
Read 9 remaining paragraphs | Comments