One of the more intriguing revelations in the most recent leak of NSA documents is the prospect that the spy agency is using browser cookies from Yahoo, Hotmail or the Google-owned DoubleClick ad network to decloak users of the Tor anonymity service.
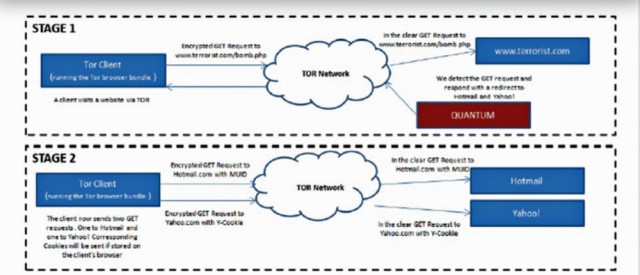
One slide from a June 2012 presentation titled "Tor Stinks" carried the heading "Analytics: Cookie Leakage" followed by the words "DoubleclickID seen on Tor and nonTor IPs." The somewhat cryptic slide led to rampant speculation on Twitter and elsewhere that the NSA and its British counterpart, the Government Communications Headquarters (GCHQ), are able to bypass Tor protections by somehow manipulating the cookies Google uses to track people who have viewed DoubleClick ads. Principal volunteers with the Tor Project believe such a scenario is "plausible," but only in limited cases. Before explaining why, it helps to discuss how such an attack might work.
As documented elsewhere in the "Tor Stinks" presentation, the spy agencies sometimes use secret servers that are located on the Internet backbone to redirect some targets to another set of secret servers that impersonate the websites the targets intended to visit. Given their privileged location, the secret backbone nodes, dubbed "Quantum," are able to respond to the requests faster than the intended server, allowing them to win a "race condition." Government spies can't track cookies within the Tor network, because traffic is encrypted during its circuitous route through three different relays. But if the spies can watch the Internet backbone, they may be able to grab or manipulate cookies once the data exits Tor and heads toward its final destination.
Read 10 remaining paragraphs | Comments




