Akamai has issued a security bulletin (PDF) about a new form of Domain Name Service-based distributed denial of service (DDoS) attacks that emerged in October, attacks that can significantly boost the volume of data flung at a targeted server. The method builds upon the well-worn DNS reflection attack method used frequently in past DDoS attacks, exploiting part of the DNS record returned by domain queries to increase the amount of data sent to the target—by stuffing it full of information from President Barack Obama’s press office.
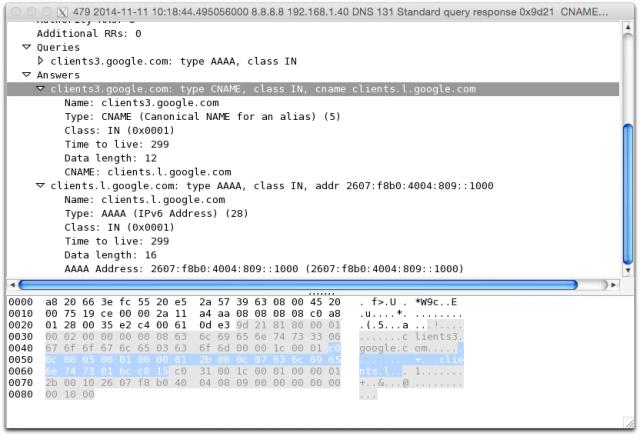
DNS reflection attacks (also known as DNS amplification attacks) use forged requests to a DNS server for the Internet Protocol address and other information about a specific host and domain name. For example, a response from Google’s DNS server typically returns something like this—a simple response with the canonical name (CNAME) of the DNS address sent in the request and an IPv4 or IPv6 address for that name:
DNS requests are usually sent using the User Datagram Protocol (UDP), which is “connectionless." It doesn’t require that a connection be negotiated between the requester and the server before data is sent to make sure it’s going to the right place. By forging the return address on the DNS request sent to make it look like it came from the target, an attacker can get a significant boost in the size of a DDoS attack because the amount of data sent in response to the DNS request is significantly larger.
Read 4 remaining paragraphs | Comments