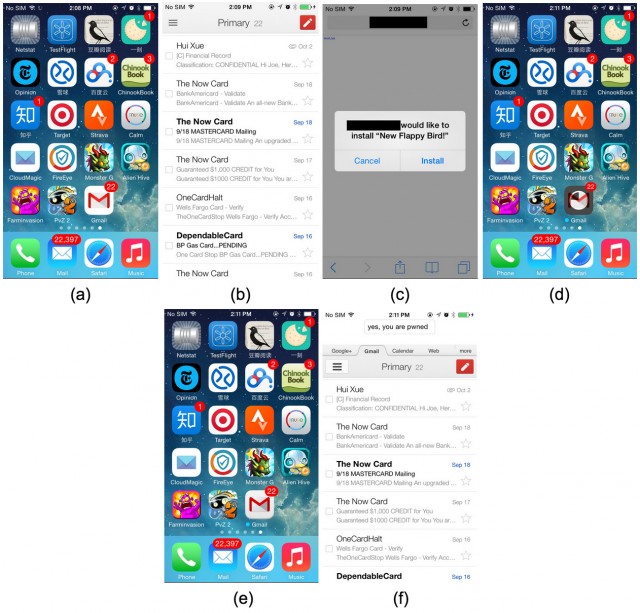
Security researchers have warned of a security hole in Apple's iOS devices that could allow attackers to replace legitimate apps with booby-trapped ones, an exploit that could expose passwords, e-mails, or other sensitive user data.
The "Masque" attack, as described by researchers from security firm FireEye, relies on enterprise provisioning to replace banking, e-mail, or other types of legitimate apps already installed on a targeted phone with a malicious one created by the adversary. From there, the attacker can use the malicious app to access sent e-mails, login credential tokens, or other data that belonged to the legitimate app.
"Masque Attacks can replace authentic apps, such as banking and e-mail apps, using attacker's malware through the Internet," FireEye researchers wrote in a blog post published Monday. "That means the attacker can steal user's banking credentials by replacing an authentic banking app with an malware that has identical UI. Surprisingly, the malware can even access the original app's local data, which wasn't removed when the original app was replaced. These data may contain cached e-mails or even login-tokens which the malware can use to log into the user's account directly."
Read 5 remaining paragraphs | Comments