Enlarge / The file names in this screenshot have been redacted to protect the vulnerable. (credit: Patrick Wardle)
Since its introduction in 2012, an OS X feature known as Gatekeeper has gone a long way to protecting the Macs of security novices and experts alike. Not only does it help neutralize social engineering attacks that trick less experienced users into installing trojans, code-signing requirements ensure even seasoned users that an installer app hasn't been maliciously modified as it was downloaded over an unencrypted connection.
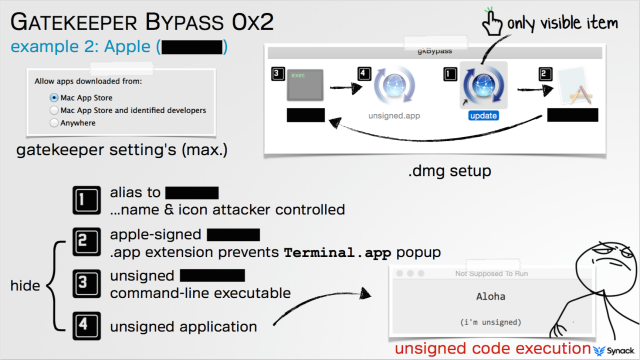
Now, a security researcher has found a drop-dead simple technique that completely bypasses Gatekeeper, even when the protection is set to its strictest setting. The hack uses a binary file already trusted by Apple to pass through Gatekeeper. Once the Apple-trusted file is on the other side, it executes one or more malicious files that are included in the same folder. The bundled files can install a variety of nefarious programs, including password loggers, apps that capture audio and video, and botnet software.
Patrick Wardle, director of research of security firm Synack, said the bypass stems from a key shortcoming in the design of Gatekeeper rather than a defect in the way it operates. Gatekeeper's sole function is to check the digital certificate of a downloaded app before it's installed to see if it's signed by an Apple-recognized developer or originated from the official Apple App Store. It was never set up to prevent apps already trusted by OS X from running in unintended or malicious ways, as the proof-of-concept exploit he developed does.