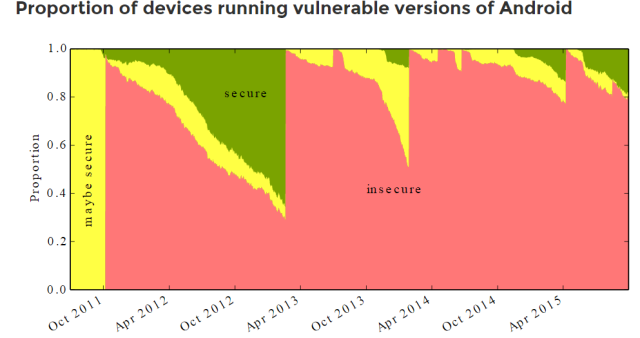
The study's estimate of the proportion of known "insecure," "maybe secure" and "secure" devices over time. (credit: androidvulnerabilities.org)
It's easy to see that the Android ecosystem currently has a rather lax policy toward security, but a recent study from the University of Cambridge put some hard numbers to Android's security failings. The conclusion finds that "on average 87.7% of Android devices are exposed to at least one of 11 known critical vulnerabilities."
Data for the study was collected through the group's "Device Analyzer" app, which has been available for free on the Play Store since May 2011. After the participants opted into the survey, the University says it collected daily Android version and build number information from over 20,400 devices. The study then compared this version information against 13 critical vulnerabilities (including the Stagefright vulnerabilities) dating back to 2010. Each individual device was then labeled "secure" or "insecure" based on whether or not its OS version was patched against these vulnerabilities, or placed in a special "maybe secure" category if it could have gotten a specialized, backported fix.
As for why so many Android devices are insecure, the study found that most of the blame sits with OEMs. The group states that "the bottleneck for the delivery of updates in the Android ecosystem rests with the manufacturers, who fail to provide updates to fix critical vulnerabilities." Along with the study, the University of Cambridge is launching "AndroidVulnerabilities.org," a site that houses this data and grades OEMs based on their security record. The group came up with a 1-10 security rating for OEMs that it calls the "FUM" score. This algorithm takes into account the number of days a proportion of running devices has no known vulnerabilities (Free), the proportion of devices that run the latest version of Android (Update), and the mean number of vulnerabilities not fixed on any device the company sells (Mean). The study found that Google's Nexus devices were the most secure out there, with a FUM score of 5.2 out of 10. Surprisingly, LG was next with 4.0, followed by Motorola, Samsung, Sony, and HTC, respectively.