
The Juniper NetScreen 5200, one of the firewalls that carries the backdoor code inserted into Juniper's ScreenOS.
On December 17, Juniper Networks issued an urgent security advisory about "unauthorized code" found within the operating system used by some of the company's NetScreen firewalls and Secure Service Gateway (SSG) appliances. The vulnerability, which may have been in place in some firewalls as far back as 2012 and which shipped with systems to customers until late 2013, allows an attacker to gain remote administrative access to systems with telnet or ssh access enabled. And now researchers have both confirmed that the backdoor exists and developed a tool that can scan for affected systems.
In a post to the Rapid7 community blog site on December 20, Metasploit project founder and Rapid7 researcher H D Moore published an analysis of the affected versions of Juniper's ScreenOS operating system, including the administrative access password that had been hard-coded into the operating system. This backdoor, which was inserted into ScreenOS versions 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20, is a change to the code that authorizes administrative access with the password "<<< %s(un='%s') = %u"—a password that Moore notes was crafted to resemble debug code to evade detection during review.
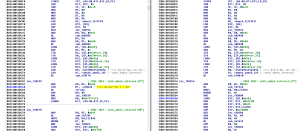
A side-by-side look at the Juniper ScreenOS code, with the backdoored code on the left and unaltered code on the right. The backdoor password is highlighted. (credit: Rapid7)
Since this code is in the firmware of the affected Juniper NetScreen and SSG appliances, the only way to remove it is to re-flash the firmware with a new version of ScreenOS. Steve Puluka has written a guide on how to perform the upgrade and avoid some of the potential problems around installation, including dealing with the configuration of a new signing key for the upgrade.