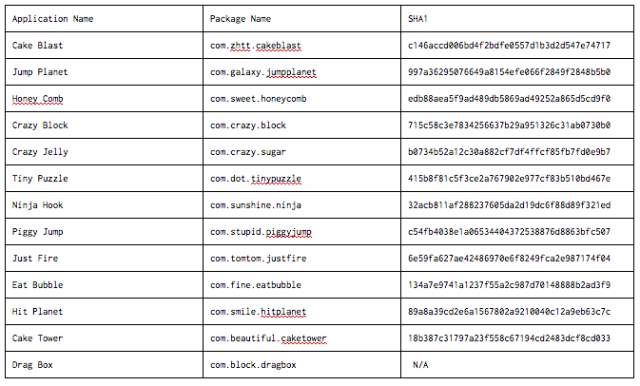
Enlarge / A list of the 13 malicious apps in the Brain Test family found hosted on Google Play. (credit: Lookout)
Google has banished 13 Android apps from its Play marketplace after security researchers found the apps made unauthorized downloads and attempted to gain root privileges that allowed them to survive factory resets.
One of the 13 apps, which was known as Honeycomb, had as many as one million downloads before it was removed, according to researchers from Lookout, the mobile security provider that spotted the malicious entries. The apps boasted a large number of downloads and highly favorable user ratings, presumably thanks to the ability of one app to automatically download other apps and then leave rave user reviews for them. In a blog post, Lookout researcher Chris Dehghanpoor wrote:
The explanation for the apps’ high ratings and hundreds-of-thousands of downloads is the malware itself. First off, some of the apps are fully-functioning games. Some are highly rated because they are fun to play. Mischievously, though, the apps are capable of using compromised devices to download and positively review other malicious apps in the Play store by the same authors. This helps increase the download figures in the Play Store. Specifically, it attempts to detect if a device is rooted, and if so, copies several files to the /system partition in an effort to ensure persistence, even after a complete factory reset. This behavior is very similar to several other malware families we’ve seen recently, specifically Shedun, ShiftyBug, and Shuanet.
As Ars reported in November, members of the Shedun, Shuanet, and ShiftyBug families expose phones to potentially dangerous root exploits that can make app removal extremely hard for many users. That's because the apps are often able to root the infected device and install themselves as system applications. That can make them hard to remove using conventional methods, such as the uninstall button or factory reset in the Android options menu.