Enlarge (credit: Blue Coat)
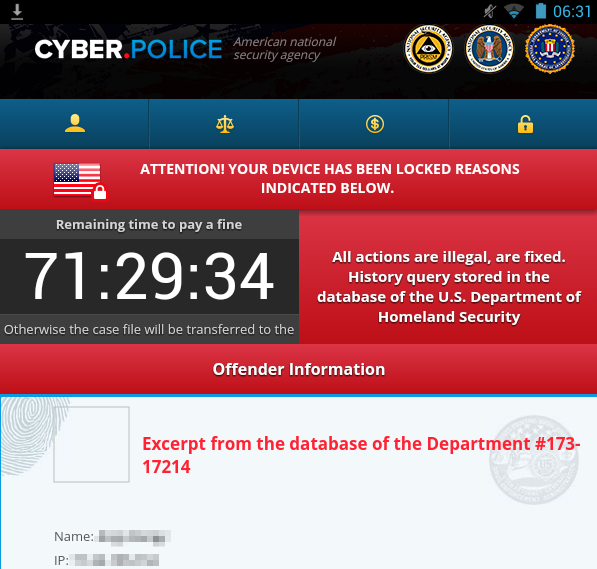
An ongoing drive-by attack is forcing ransomware onto Android smartphones by exploiting critical vulnerabilities in older versions of Google's mobile operating system still in use by millions of people, according to research scheduled to be published Monday.
The attack combines exploits for at least two critical vulnerabilities contained in Android versions 4.0 through 4.3, including an exploit known as Towelroot, which gives attackers unfettered "root" access to vulnerable phones. The exploit code appears to borrow heavily from, if not copy outright, some of these Android attack scripts, which leaked to the world following the embarrassing breach of Italy-based Hacking Team in July. Additional data indicates devices running Android 4.4 may also be infected, possibly by exploiting a different set of vulnerabilities.
It's the first time—or at least one of only a handful of times—Android vulnerabilities have been exploited in real-world drive-by attacks. For years, most Android malware has spread by social engineering campaigns that trick a user into installing a malicious app posing as something useful and benign. The drive-by attack—which has been active for at least the past 60 days and was discovered by security firm Blue Coat Systems—is notable because it's completely stealthy and requires no user interaction on the part of the end user. The company's findings have been published here.