A surprisingly large number of developers are posting their Slack login credentials to GitHub and other public websites, a practice that in many cases allows anyone to surreptitiously eavesdrop on their conversations and download proprietary data exchanged over the chat service.
According to a blog post published Thursday, company researchers recently estimated that about 1,500 access tokens were publicly available, some belonging to people who worked for Fortune 500 companies, payment providers, Internet service providers, and health care providers. The researchers privately reported their findings to Slack, and the chat service said it regularly monitors public sites for posts that publish the sensitive tokens.
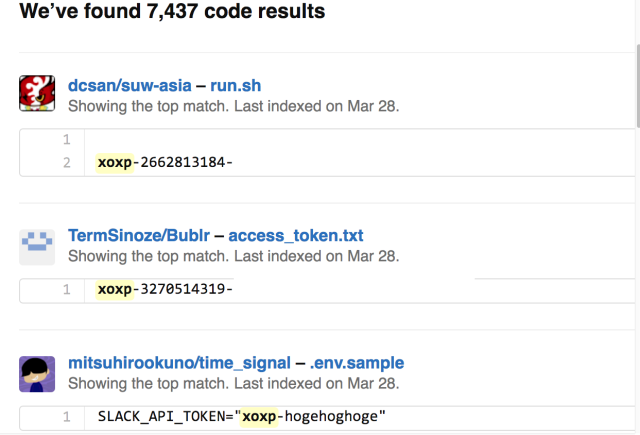
Still, a current search on GitHub returned more than 7,400 pages containing "xoxp." That's the prefix contained in tokens that in many cases allow automated scripts to access a Slack account, even when it's protected by two-factor authentication. A separate search uncovered more than 4,100 Slack tokens with the prefix "xoxb." Not all results contained the remainder of the token that's required for logging in, but many appeared to do just that. By including valid tokens in code that's made available to the world, developers make it possible for unscrupulous people to access the private conversations between the developers and the companies they work for and to download files and private Web links they exchange.