(credit: Cao et al.)
Computer scientists have discovered a serious Internet vulnerability that allows attackers to terminate connections between virtually any two parties and, if the connections aren't encrypted, inject malicious code or content into the parties' communications.
The vulnerability resides in the design and implementation of RFC 5961, a relatively new Internet standard that's intended to prevent certain classes of hacking attacks. In fact, the protocol is designed in a way that it can easily open Internet users to so-called blind off-path attacks, in which hackers anywhere on the Internet can detect when any two parties are communicating over an active transmission control protocol connection. Attackers can go on to exploit the flaw to shut down the connection, inject malicious code or content into unencrypted data streams, and possibly degrade privacy guarantees provided by the Tor anonymity network.
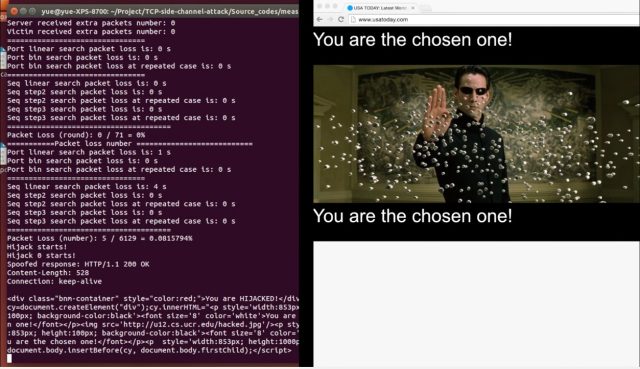
At the 25th Usenix Security Symposium on Wednesday, researchers with the University of California at Riverside and the US Army Research Laboratory will demonstrate a proof-of-concept exploit that allows them to inject content into an otherwise legitimate USA Today page that asks viewers to enter their e-mail and passwords. The malicious, off-site JavaScript code attack is possible because the vulnerable USA Today pages aren't encrypted. Even if they were protected, attackers could still terminate the connection. Similar attacks work against a variety of other unidentified sites and services, as long as they have long-lived connections that give hackers enough time—roughly 60 seconds—to carry out the attack.