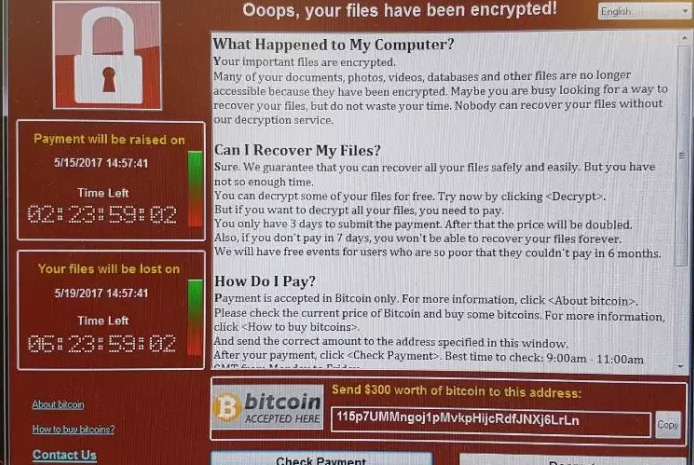
Enlarge (credit: Health Service Journal)
A day after a ransomware worm infected 75,000 machines in 100 countries, Microsoft is taking the highly unusual step of issuing patches that immunize Windows XP, 8, and Server 2003, operating systems the company stopped supporting as many as three years ago.
Microsoft also rolled out a signature that allows its Windows Defender antivirus engine to provide "defense-in-depth" protection. The moves came after attackers on Friday used a recently leaked attack tool developed by the National Security Agency to virally spread ransomware known as "WCry" or "WannaCrypt." Within hours, computer systems around the world were crippled, prompting hospitals to turn away patients while telecoms, banks, and companies such as FedEx were forced to turn off computers for the weekend.
The chaos surprised many security watchers because Microsoft issued an update in March that patched the underlying vulnerability in Windows 7 and most other supported versions of Windows. (Windows 10 was never vulnerable.) Friday's events made it clear that enough unpatched systems exist to cause significant outbreaks that could happen again in the coming days or months. In a blog post published late Friday night, Microsoft officials wrote: