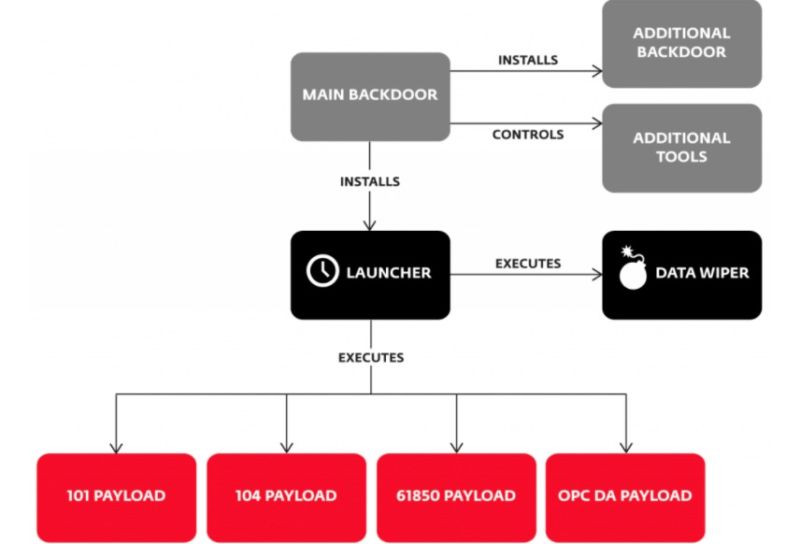
Enlarge / An overview of Crash Override/Industroyer, including the four international specifications it uses to communicate with electric grid devices all over the world. (credit: Eset)
Last December, hackers with suspected ties to Russia caused a power outage in Ukraine in a deliberate attempt to leave households without electricity during what's typically one of the coldest months of the year. Now, the advanced malware that triggered the power failure has been found in the wild. This discovery is prompting concerns that the attack tools could be repurposed or reused in new sabotage operations, possibly by unrelated hacking groups.
"Crash Override," as security firm Dragos has named the tool platform, is the first known malware framework designed to attack electric grid systems. Dragos researchers said it was used successfully in what may have been a dress rehearsal on a December 17 hack on an electric transmission substation in Kiev. While the Kiev outage lasted only a few hours, several features of the malware that weren't turned on in the December hack have the potential to cause disruptions that persist for as long as a week. Crash Override is a completely new platform that was far more advanced than the general-purpose tools the same group used to attack Ukraine's power grid in December 2015.
What makes Crash Override so sophisticated is its ability to use the same arcane technical protocols that individual electric grid systems rely on to communicate with one another. As such, the malware is more notable for its mastery of the industrial processes used by global grid operators than its robust code. Its fluency in the low-level grid languages allowed it to instruct Ukrainian devices to de-energize and re-energize substation lines, a capability not seen in the attack a year earlier that used a much cruder set of tools and techniques. The concern is that "Industroyer"—the other name given to the malware—can be used against a broad range of electric systems around the world.