Authored by SangRyol Ryu and Yukihiro Okutomi
McAfee’s Mobile Research team recently analyzed new malware targeting NTT DOCOMO users in Japan. The malware which was distributed on the Google Play store pretends to be a legitimate mobile security app, but it is in fact a payment fraud malware stealing passwords and abusing reverse proxy targeting NTT DOCOMO mobile payment service users. McAfee researchers notified Google of the malicious apps, スマホ安心セキュリティ, or ‘Smartphone Anshin Security’, package name ‘com.z.cloud.px.app’ and ‘com.z.px.appx’. The applications are no longer available on Google Play. Google Play Protect has also taken steps to protect users by disabling the apps and providing a warning. McAfee Mobile Security products detect this threat as Android/ProxySpy and protect you from malware. For more information, to get fully protected, visit McAfee Mobile Security.
How Do victims install this malware?
The malware actor continues to publish malicious apps on the Google Play Store with various developer accounts. According to the information posted on Twitter by Yusuke Osumi, Security Researcher at Yahoo! Japan, the attacker sends SMS messages from overseas with a Google Play link to lure users to install the malware. To attract more users, the message entices users to update security software.
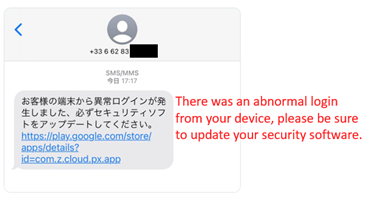
A SMS message from France (from Twitter post by Yusuke)
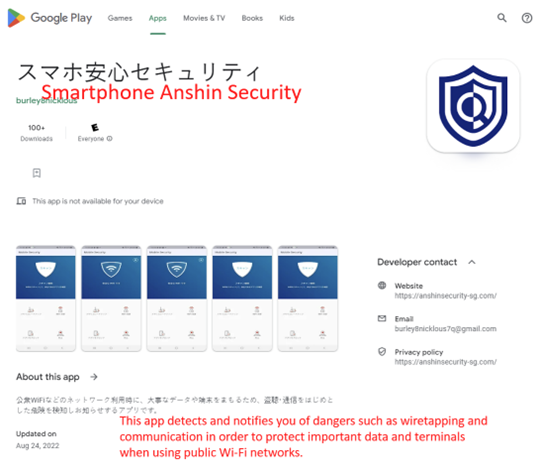
Malware on Google Play
The Mobile Research team also found that the malware actor uses Google Drive to distribute the malware. In contrast to installing an application after downloading an APK file, Google Drive allows users to install APK files without leaving any footprint and makes the installation process simpler. Once the user clicks the link, there are only a few more touches required to run the application. Only three clicks are enough if users have previously allowed the installation of unknown apps on Google Drive.
Following notification from McAfee researchers, Google has removed known Google Drive files associated with the malware hashes listed in this blog post.
What does this malware look like?
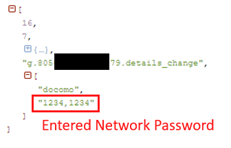
When an NTT DOCOMO network user installs and launches this malware, it asks for the Network password. Cleverly, the malware shows incorrect password messages to collect more precise passwords. Of course, it does not matter whether the password is correct or not. It is a way of getting the Network password.
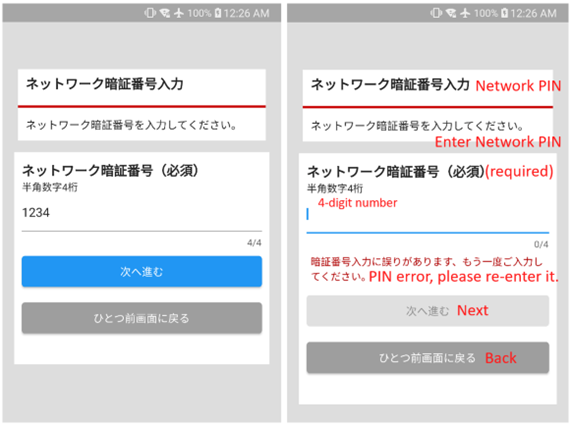
The Network password is used for the NTT DOCOMO payment service which provides easy online payments. NTT DOCOMO mobile network users can start this payment service by just setting 4-digits password called a Network password. The charge will be paid along with the mobile phone bill. When you need to pay online, you can simply do the payment process by entering the 4-digits password.
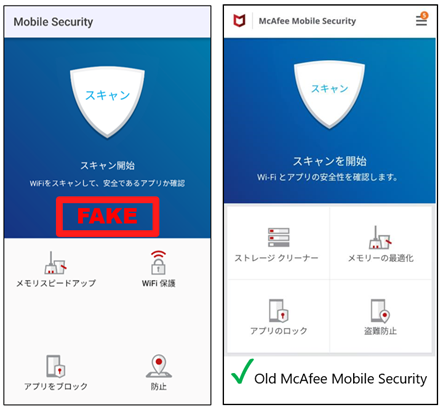
After the password activity, the malware shows a fake mobile security screen. Interestingly, the layout of the activity is similar to our old McAfee Mobile Security. All buttons look genuine, but these are all fake.
How does this malware work?
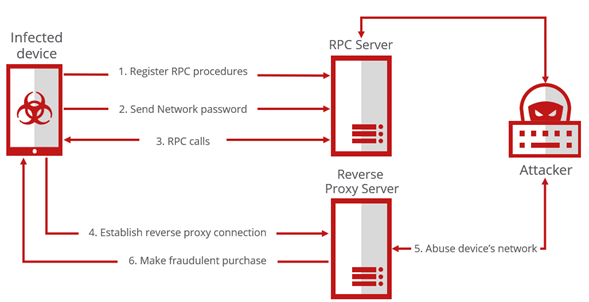
There is a native library named ‘libmyapp.so’ loaded during the app execution written in Golang. The library, when loaded, tries to connect to the C2 server using a Web Socket. Web Application Messaging Protocol (WAMP) is used to communicate and process Remote Procedure Calls (RPC). When the connection is made, the malware sends out network information along with the phone number. Then, it registers the client’s procedure commands described in the table below. The web socket connection is kept alive and takes the corresponding action when the command is received from the server like an Agent. And the socket is used to send the Network password out to the attacker when the user enters the Network password on the activity.
| RPC Function name | Description |
| connect_to | Create reverse proxy and connect to remote server |
| disconnect | Disconnect the reverse proxy |
| get_status | Send the reverse proxy status |
| get_info | Send line number, connection type, operator, and so on |
| toggle_wifi | Set the Wi-Fi ON/OFF |
| show_battery_opt | Show dialog to exclude battery optimization for background work |
Registered RPC functions description

To make a fraudulent purchase by using leaked information, the attacker needs to use the victim’s mobile network. The RPC command ‘toggle_wifi’ can switch the Wi-Fi connection status of the victim, and ‘connect_to’ will provide a reverse proxy to the attacker. A reverse proxy can allow connecting the host behind a NAT (Network Address Translation) or a firewall. Via the proxy, the attacker can send purchase requests via the victim’s mobile network.
Conclusion
It is interesting that the malware uses a reverse proxy to steal the user’s network and implement an Agent service with WAMP. McAfee Mobile Research Team will continue to find this kind of threat and protect our customers from mobile threats. It is recommended to be more careful when entering a password or confidential information into untrusted applications.
IoCs (Indicators of Compromise)
193[.]239[.]154[.]23
91[.]204[.]227[.]132
ruboq[.]com
| SHA256 | Package Name | Distribution |
| 5d29dd12faaafd40300752c584ee3c072d6fc9a7a98a357a145701aaa85950dd | com.z.cloud.px.app | Google Play |
| e133be729128ed6764471ee7d7c36f2ccb70edf789286cc3a834e689432fc9b0 | com.z.cloud.px.app | Other |
| e7948392903e4c8762771f12e2d6693bf3e2e091a0fc88e91b177a58614fef02 | com.z.px.appx | Google Play |
| 3971309ce4a3cfb3cdbf8abde19d46586f6e4d5fc9f54c562428b0e0428325ad | com.z.cloud.px.app2 | Other |
| 2ec2fb9e20b99f60a30aaa630b393d8277949c34043ebe994dd0ffc7176904a4 | com.jg.rc.papp | Google Drive |
| af0d2e5e2994a3edd87f6d0b9b9a85fb1c41d33edfd552fcc64b43c713cdd956 | com.de.rc.seee | Google Drive |
The post Fake Security App Found Abuses Japanese Payment System appeared first on McAfee Blog.