Over the past two weeks, a new wave of Web attacks has battered major US banks, causing disruptions for many of their online services. Now, an Israel-based security firm has uncovered one of the secret footsoldiers behind the mass assault: a compromised website that was rigged to unleash a torrent of junk traffic on three of the world's biggest financial institutions.
The discovery by Web application security firm Incapsula helps explain the strategy behind the four-month-old campaign, which has been carried out under the flag of a group calling itself Izz ad-Din al-Qassam—rather than compromise and recruit thousands or tens of thousands of end-user PCs to carry out the distributed denial-of-service attacks, why not target a handful of Web servers that have orders of magnitude more bandwidth and processing power?
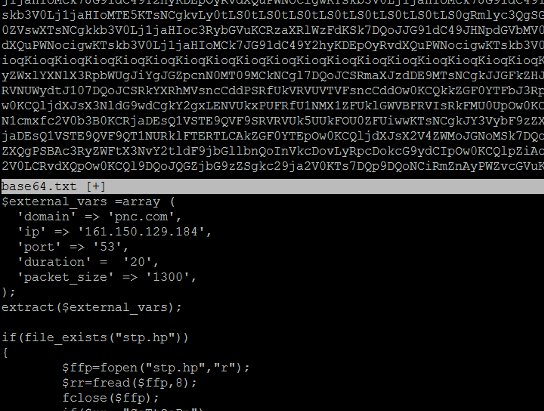
Over the weekend, Incapsula researchers noticed a general-interest website located in the UK that was exhibiting suspicious behavior. They quickly discovered a backdoor that had been planted on it that was programmed to receive instructions from remote attackers. An analysis showed the website, which had just recently contracted with Incapsula, was being directed to send a flood of HTTP and UDP packets to major banks including PNC Financial Services, HSBC, and Fifth Third Bank.
Read 7 remaining paragraphs | Comments