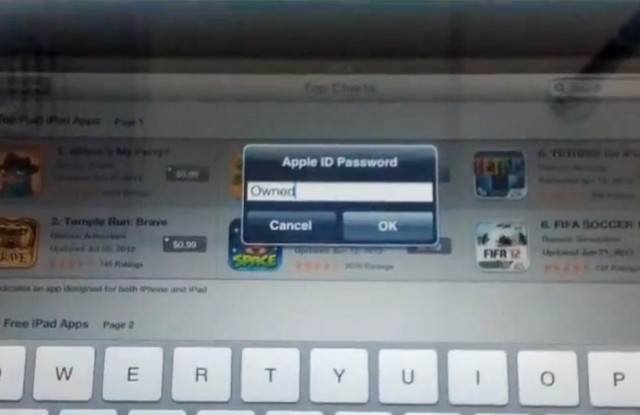
For the past nine months—and possibly for years—Apple has unnecessarily left many of its iOS customers open to attack because engineers failed to implement standard technology that encrypts all traffic traveling between handsets and the company's App Store.
While HTTPS-encrypted communications have been used for years to prevent attackers from intercepting and manipulating sensitive traffic sent by online banks and merchants, the native iOS app that connects to Apple's App Store fully deployed the protection only recently. Elie Bursztein, a Google researcher who said he discovered the security hole in his spare time, said in a blog post published on Friday that he reported various iOS flaws to Apple's security team in July. His post gave no indication that the iOS app had ever fully used HTTPS, raising the possibility that this significant omission has been present for years. (Apple doesn't comment on security matters, so it's impossible for Ars to confirm the precise timeline or level of protection.)
As most Ars readers know, HTTPS is a basic security measure that's almost as old as the Web itself. It ensures that traffic traveling between an end-user and a webserver is encrypted. That prevents anyone who may have a connection between the two endpoints from listening in. HTTPS also provides cryptographic assurance that the server answering calls to itunes.apple.com truly belongs to Apple and not an impostor. Over the past five years, a growing roster of companies including Google, Facebook, and Twitter have begun offering end-to-end HTTPS, making it harder for attackers to use age-old exploits that bypass the measure. It's unclear why it has taken Apple so long to catch up.
Read 5 remaining paragraphs | Comments