A change in some early versions of Google's Chrome browser is attracting the attention of security researchers who say it can make it harder for end users to know when they're visiting a malicious site trying to push malware or phish login credentials.
The change, which is said to affect a small fraction of people running version 36 of Chrome, aka Canary, causes the browser's address bar (Google calls it the Omnibox) to no longer display the URL currently open. Instead, the domain name and any subdomains of the open page are shown immediately to the left of the Omnibox in what's dubbed the Origin Chip. Google developers haven't given a definitive explanation for the experimental change, although Jake Archibald, a developer advocate for Google Chrome, recently gave his personal thoughts here. Presumably, it's designed to keep up with various features already available in Internet Explorer, Firefox, and Safari that highlight the precise domain a browser is visiting. The features are designed to thwart attacks that rely on long, confusing addresses that can sometimes conceal the true domain that's open.
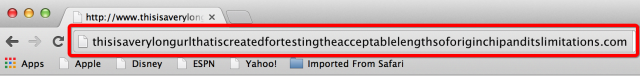
Researchers at PhishMe, a company that helps prevent organizations from falling victim to phishing and malware attacks, have been testing the trial interface and have found behavior they say could make it easier for attackers to fool end users. By loading up an address with long strings of characters, the researchers were able to completely suppress both the domain name and other address parameters in both the Omnibox and Origin Chip. For instance, when the PhishMe researchers entered the URL "hxxp://this.is.a.test.for.longurl.to.test.the.canary.property.in.the.new.chrome.browser.and.see.if.it.works.DOMAINNAME.com/CheckingNowWithSampleURLInHere/eb31ac/?login_id=48ea2b9a-4f1b-4bbb-b573-89524db025e9" (minus the quotes), the Chrome interface looked like this:
Read 4 remaining paragraphs | Comments