Digital rights advocates are doubling down on their criticism of a US-based ISP suspected of performing encryption downgrade attacks that caused customers' e-mail to remain in plaintext as it passed over the Internet.
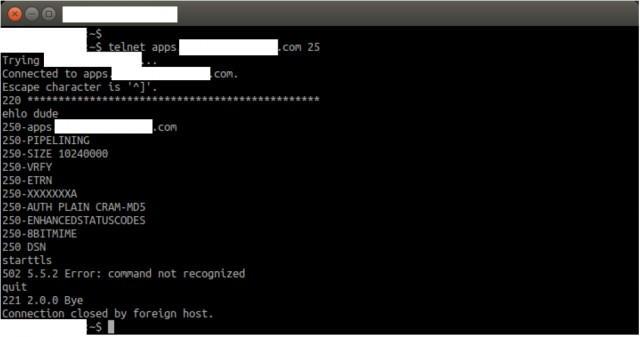
The attacks, according to researchers, were carried out by AT&T subsidiary Cricket and prevented e-mail from being protected by STARTTLS, a technology that uses the secure sockets layer or transport layer security protocols to encrypt plaintext communications. The attacks worked by removing the STARTTLS flag that causes e-mail to be encrypted as it passes from the sending server to the receiving server. After the tampering came to light late last month it was reported by The Washington Post and TechDirt.
"It is important that ISPs immediately stop this unauthorized removal of their customers' security measures," wrote Electronic Frontier Foundation staff technologist Jacob Hoffman-Andrews in a blog post published Tuesday. "ISPs act as trusted gateways to the global Internet, and it is a violation of that trust to intercept or modify client traffic, regardless of what protocol their customers are using. It is a double violation when such modification disables security measures their customers use to protect themselves."
Read 2 remaining paragraphs | Comments