Enlarge (credit: Vectra Networks)
For more than two decades, Microsoft Windows has provided the means for clever attackers to surreptitiously install malware of their choice on computers that connect to booby-trapped printers, or other devices masquerading as printers, on a local area network. Microsoft finally addressed the bug on Tuesday during its monthly patch cycle.
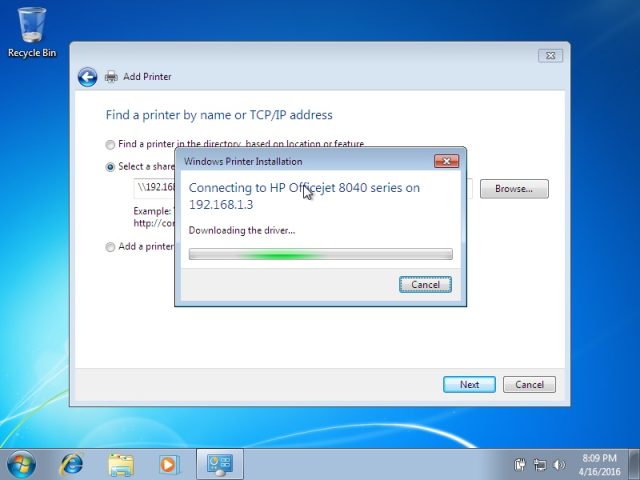
The vulnerability resides in the Windows Print Spooler, which manages the process of connecting to available printers and printing documents. A protocol known as Point-and-Print allows people who are connecting to a network-hosted printer for the first time to automatically download the necessary driver immediately before using it. It works by storing a shared driver on the printer or print server and eliminates the hassle of the user having to manually download and install it.
Researchers with security firm Vectra Networks discovered that the Windows Print Spooler doesn't properly authenticate print drivers when installing them from remote locations. The failure makes it possible for attackers to use several different techniques that deliver maliciously modified drivers instead of the legitimate one provided by the printer maker. The exploit effectively turns printers, printer servers, or potentially any network-connected device masquerading as a printer into an internal drive-by exploit kit that infects machines whenever they connect.