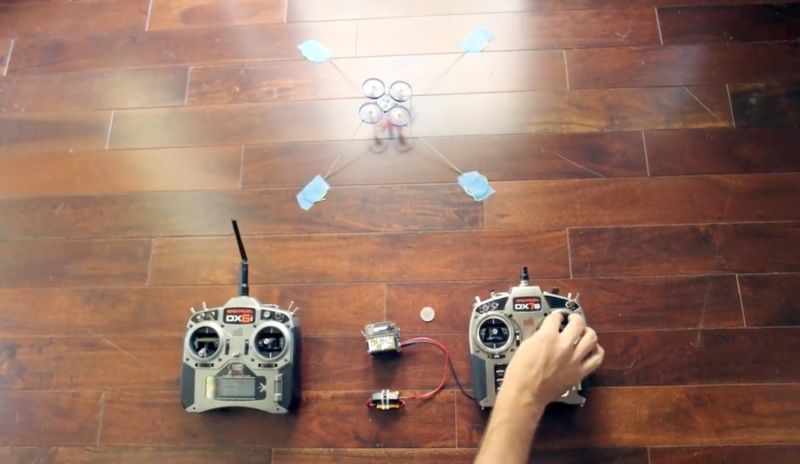
Enlarge / Using the attached device, an attacker's remote control on the right is able to hijack the original remote control on the left. (credit: Jonathan Andersson)
The advent of inexpensive consumer drones has generated a novel predicament for firefighters, law-enforcement officers, and ordinary citizens who encounter crafts they believe are interfering with their safety or privacy. In a series of increasingly common events—several of them chronicled by Ars—drones perceived as trespassing have been blown out of the sky with shotguns. Firefighters have also complained that hobbyist drones pose a significant threat that sometimes prompts them to ground helicopters.
Now, a researcher has demonstrated a significantly more subtle and proactive remedy that doesn't involve shotgun blasts or after-the-fact arrests by law enforcement. It's a radio transmitter that seizes complete control of nearby drones as they're in mid-flight. From then on, the drones are under the full control of the person with the hijacking device. The remote control in the possession of the original operator experiences a loss of all functions, including steering, acceleration, and altitude. The hack works against any drone that communicates over DSMx, a widely used remote control protocol for operating hobbyist drones, planes, helicopters, cars, and boats.
Besides hijacking a drone, the device provides a digital fingerprint that's unique to each craft. The fingerprint can be used to identify trusted drones from unfriendly ones and potentially to provide forensic evidence for use in criminal or civil court cases. Unlike most other counter-drone technologies publicly demonstrated to date, it isn't a frequency jammer that merely prevents a remote control from communicating with a drone. Instead, it gives the holder the ability to completely seize control of the unmanned craft. It was presented on Wednesday at the PacSec 2016 security conference in Tokyo by Jonathan Andersson, the advanced security research group manager at Trend Micro's TippingPoint DVLab division.