(credit: Malwarebytes)
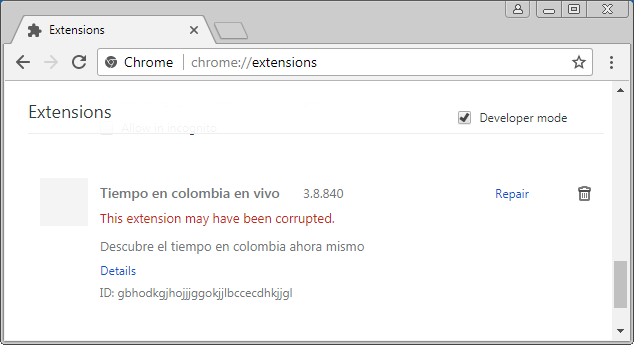
Proving once again that Google Chrome extensions are the Achilles heel of what's arguably the Internet's most secure browser, a researcher has documented a malicious add-on that tricks users into installing it and then is nearly impossible for most to manually uninstall. It was available for download on Google servers until Wednesday, 19 days after it was privately reported to Google security officials, a researcher said.
Once installed, an app called "Tiempo en colombia en vivo" prevents users from accessing the list of installed Chrome extensions by redirecting requests to chrome://apps/?r=extensions instead of chrome://extensions/, the page that lists all installed extensions and provides an interface for temporarily disabling or uninstalling them. Malwarebytes researcher Pieter Arntz said he experimented with a variety of hacks—including disabling JavaScript in the browser, starting Chrome with all extensions disabled, and renaming the folder where extensions are stored—none of them worked. Removing the extension proved so difficult that he ultimately advised users to run the free version of Malwarebytes and let it automatically remove the add-on.
When Arntz installed the extension on a test machine, Chrome spontaneously clicked on dozens of YouTube videos, an indication that inflating the number of views was among the things it did. The researcher hasn't ruled out the possibility that the add-on did more malicious things because the amount of obfuscated JavaScript it contained made a comprehensive analysis too time consuming. The researcher provided additional details in a blog post published Thursday.